SharePoint is providing multiple scopes or the permission to provide flexibility to the admins and the developers to control who can access what.
Scopes
The following table lists the Selected permission scopes.Expand table
| Scopes | Description |
|---|---|
| Sites.Selected | Manages application access at the site collection level, providing access to a specific site collection |
| Lists.SelectedOperations.Selected | Manages application access at the list level, providing access to a specific list |
| ListItems.SelectedOperations.Selected | Manages application access at the files, list item, or folder level, providing access to one or more list items |
| Files.SelectedOperations.Selected | Manages application access at the file or library folder level, providing access to one or more files |
What permissions do I need to manage permissions?
The permission requirements vary by level. In all delegated, cases the current user also needs sufficient permissions to manage access by calling the API. The following table includes scopes and scopes + assigned roles to the parent resource.
| Resource | Required resource permissions |
|---|---|
| site | Sites.FullControl.All |
| list | Sites.FullControl.All, Sites.Selected+FullControl, Sites.Selected+Owner |
| listItem | Sites.FullControl.All, Sites.Selected+FullControl, Sites.Selected+Owner, Lists.SelectedOperations.Selected+FullControl, Lists.SelectedOperations.Selected+Owner |
| file | Sites.FullControl.All, Sites.Selected+FullControl, Sites.Selected+Owner, Lists.SelectedOperations.Selected+FullControl, Lists.SelectedOperations.Selected+Owner |
Steps to setup the app
- Navigate to Home – Microsoft Azure
- Then go to Microsoft Entra –> apps registration
- Select “new registration” and follow the steps.
- Grant the permission on list level as in the following level
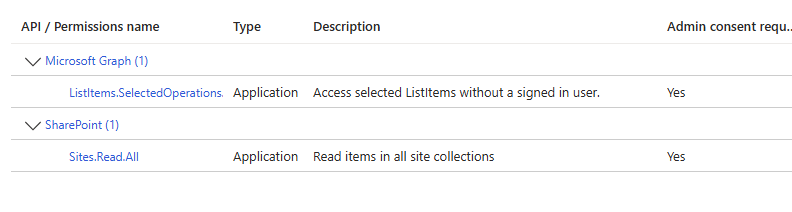
Site collection information:
- Site ID: {siteID}
- List ID: {ListID}
POST request: “https://graph.microsoft.com/beta/sites/{siteID}/lists/{listID}/permissions” and the body of the request paste the following:
{
"roles": ["read"],
"grantedTo": {
"application": {
"id": "555a66f4-2948-4b13-a675-0d6b03baca42"
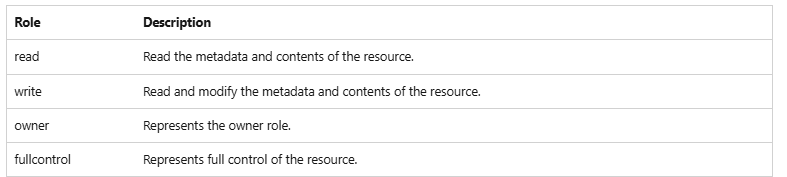
}}}In the following table, you can see all the available permissions to be granted on list level
Also, you can validate and check for the granted permission by sending a get request to the same end point you used to apply the permission. You should be able to see the permission as in the following image:

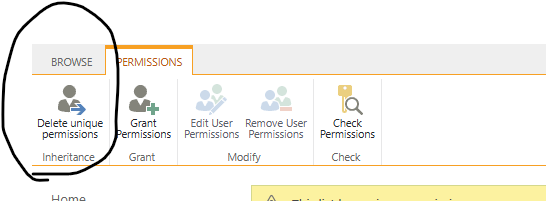
One more check, if you navigated to the List from browser, you will see that the list is not inheriting anymore and has unique permissions:
Let’s perform the CSOM test:
Instantiate the context – you can refer to sites.selected article for ore details about the setup
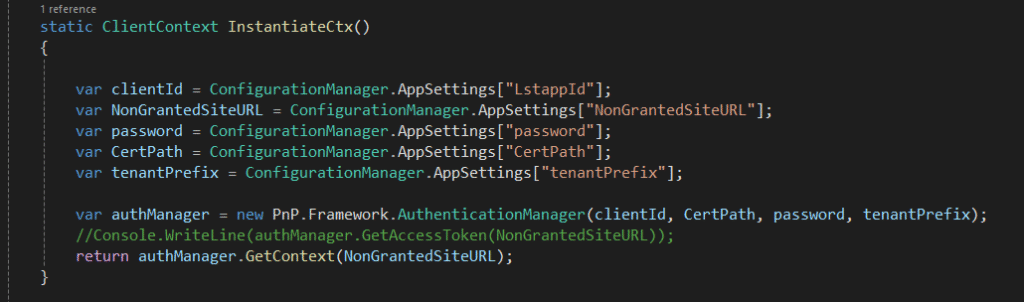
Using the instantiated context to get the data from the list:
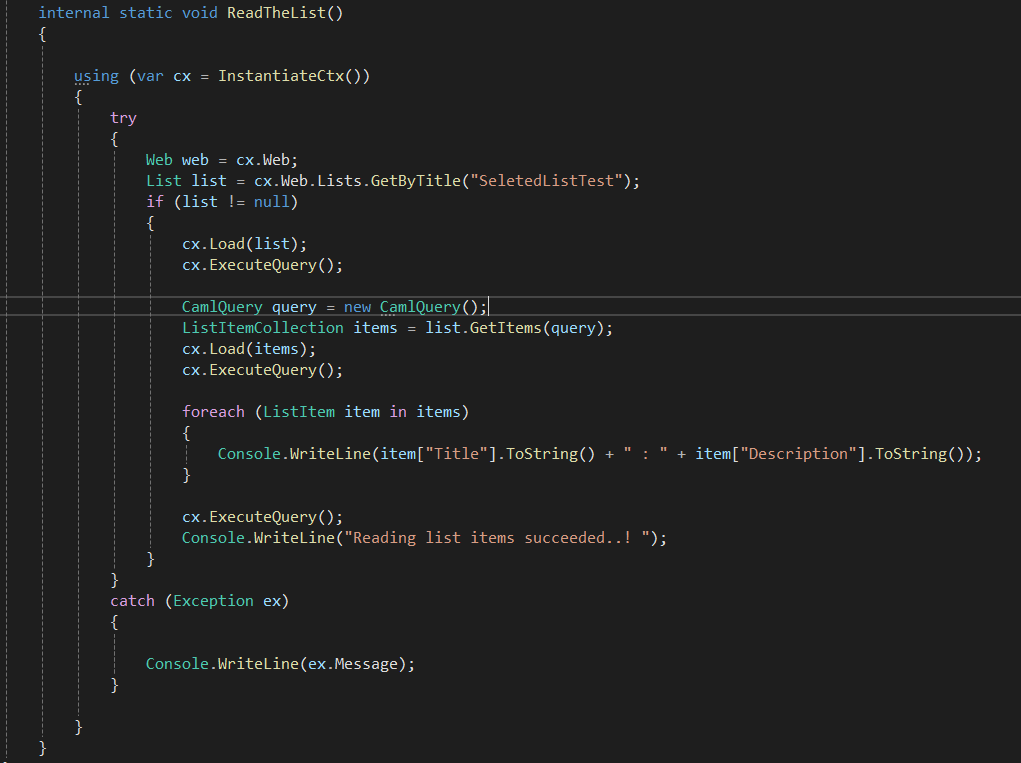
using (var cx = InstantiateCtx())
{
try
{
Web web = cx.Web;
List list = cx.Web.Lists.GetByTitle("SeletedListTest");
if (list != null)
{
cx.Load(list);
cx.ExecuteQuery();
CamlQuery query = new CamlQuery();
ListItemCollection items = list.GetItems(query);
cx.Load(items);
cx.ExecuteQuery();
foreach (ListItem item in items)
{
Console.WriteLine(item["Title"].ToString() + " : " + item["Description"].ToString());
}
cx.ExecuteQuery();
Console.WriteLine("Reading list items succeeded..! ");
}
}
catch (Exception ex)
{
Console.WriteLine(ex.Message);
}
} 